I just wanted to take a short moment and tell everyone on my blog about the latest news about TS Session hijacking. Mainly noted here: http://www.korznikov.com/2017/03/0-day-or-feature-privilege-escalation.html
My two cents on this: "Calm down, Spread out, nothing to see here!"
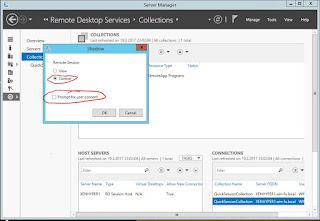
This a normal feature of the OS that I use daily on my lab server where my students use VM's on. The OS is the same for the server and the client below the surface so you can do this on a client or a server for that reason. This "Feature" is known as shadowing.
Here's a few screen shots where I "HIJACK" a session and do "PRIVILEGE ELEVATION!!"
So any Admin can do this not just SYSTEM and not just with a Service.
With SYSTEM you get the privilege of attaching to disconnected sessions - that is a nice bonus. Just remember if you want to show the session hijack thing it's a lot easier by running PSEXEC -SID TASKMGR.exe
Then go to Users tab and choose who you want to be. No service needed and works on all OS's.
Also a good point once again that you can't allow Domain Admins to log on to normal workstations as they could be compromised and someone can use this trick against him.
With SYSTEM you get the privilege of attaching to disconnected sessions - that is a nice bonus. Just remember if you want to show the session hijack thing it's a lot easier by running PSEXEC -SID TASKMGR.exe
Then go to Users tab and choose who you want to be. No service needed and works on all OS's.
Also a good point once again that you can't allow Domain Admins to log on to normal workstations as they could be compromised and someone can use this trick against him.
Cheers,
Sami

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.