Because of the current state of cybersecurity, and to protect the COMPANY networks in Ukraine, I have decided to publish easy to implement and free instructions for protecting Windows environments against an invader. Read the whole thread and if you find it useful à Retweet!
I could tell you that you should remove
end-user admin rights, deploy AppLocker etc. but in reality those are not done
in a matter of days. So these instructions are meant to give fast gains and
real-life effect in defending against cyber-attacks.
At the end of the day, security is simple.
It’s more about correct ways of operating, concepts, than expensive products.
In this thread I’m going through what I would personally do if I was at war and
protections would have to upped to the next level in hours without
disconnecting the systems from the Internet.
The instructions are meant to prevent
losing your biggest treasure – the Directory Service. A few soldiers might be
lost but the directory service will not be compromised. Companies don’t get on
the news by having ransomware on one computer, but by someone controlling the
whole infrastructure and keeping your operations as hostage.
These instructions are simple and apply to
any company that uses a Directory Service (AD/AAD). These could be better by
taking time with the customer and tailoring it for them – but now I aim to
build instructions that work for most if not all.
You can always create better but remember
that “in security, don’t let perfect be the enemy of good”. Now we need to
DEPLOY things FAST so that innocent companies stay safe! There’s no time for
“This is only 99% secure” or “There is probably a way around this”.
We need to make things BETTER, NOW! We can tweak and harden later, when we have the basics deployed.
1. Tier0-isolation. The holy grail of every attacker is a Domain Admin account. So that DA’s can’t be stolen, we block them from being used anywhere else than where they are needed. Link the following policy to every computer except your DC’s.
Since you can’t use DA to manage anything but DC’s, you need to add the following setting to the policy, so that members of ComputerAdmins can manage the other computers.
3. Same for Azure. You can achieve
the same even if settings are not exactly the same. These pics show how I do it
and how I block limited users from accessing the portal.. https://techcommunity.microsoft.com/t5/intune-customer-success/new-settings-available-to-configure-local-user-group-membership/ba-p/3093207
You can later tweak and split your AD into more tiers, deploy PAWs etc. Now the Tier0 isolation is the one you MUST DO NOW!
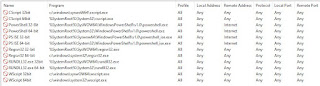
2. Containing PowerShell. PS is used by almost all malware. It attacks, takes orders and sends precious information to the attacker. So, let’s block it by adding Outbound Firewall Rules to the policy as seen in the pic:





No comments:
Post a Comment
Note: Only a member of this blog may post a comment.